Deepfactor is added to your application in a language agnostic manner. It collects telemetry from your running application and generates security insights. In order to enhance insights, we also provide programming language specific agents which can be injected when you run your application with Deepfactor.
The LSA provides the following additional capabilities:
Language specific stack trace frame information #
Deepfactor by default shows the native stack trace frames. LSA is used to collect interpreted language stack trace frames.
This capability is enabled by default. If you want to disable this functionality, you can perform the following steps.
- dfctl run
If you are running your application using Deepfactor command line utility (dfctl), then you can pass the option –disable-stack-traces (optional). - docker build
If you are building Deepfactor enabled container images (to be used in container orchestration platforms), then you need to pass the following additional build arg
–build-arg “DF_STACK_TRACES=disable” - Kubernetes admission webhook
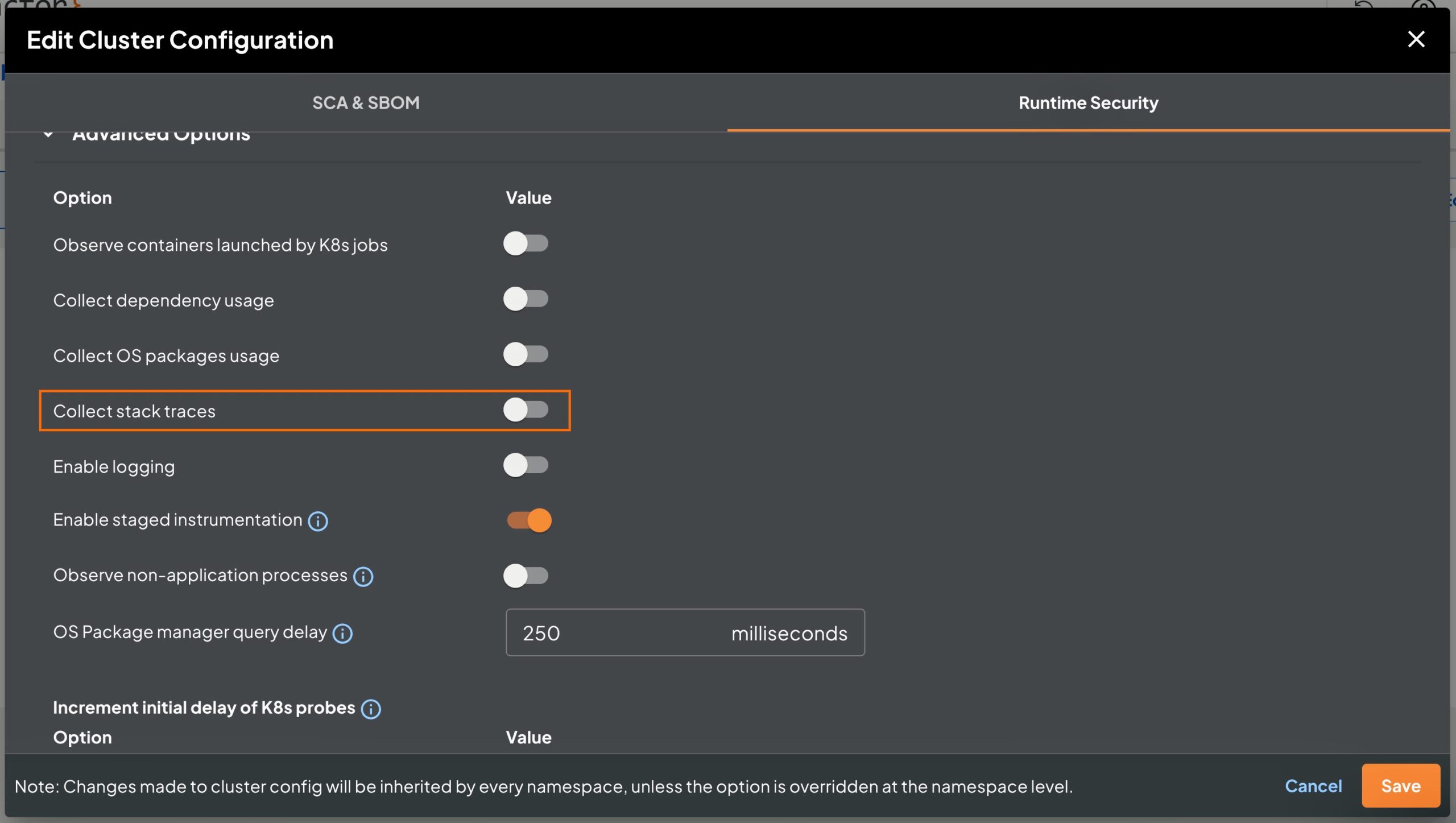
If you are using the K8s admission webhook, then you can edit the cluster configuration from the portal UI. Click on Kubernetes Clusters on the left sidebar. Then locate and click on the name cluster in you would like to disable stack trace collection. Then click on Cluster configuration tab followed by Edit Config button. On the Edit Cluster Configuration dialog, select Runtime Security and open Advanced options accordion. Turn off ‘Collect stack traces’ option.
Usage tracking #
Deepfactor can keep track usage of application dependencies at runtime. This usage information will help you understand the extent of usage of your dependencies and help you prioritize which vulnerable dependencies to update/replace. For java applications, Deepfactor injects a jvmti agent which intercepts every class load event. This can add a non-trivial amount of overhead, particularly at startup depending upon the complexity of your application. For interpreted language (Node.js, python, Ruby and PHP) dependencies, usage tracking is enabled always and does not add any additional overhead.
To disable usage tracking for java applications, please follow the below instructions
- dfctl run
If you are running your application using the Deepfactor command line utility (dfctl), then you can pass the option –disable-usage-tracking. - docker build
If you are building Deepfactor enabled container images (to be used in container orchestration platforms), then you need to pass the following additional build arg
–build-arg “DF_USAGE_TRACKING=enable” - Kubernetes admission webhook
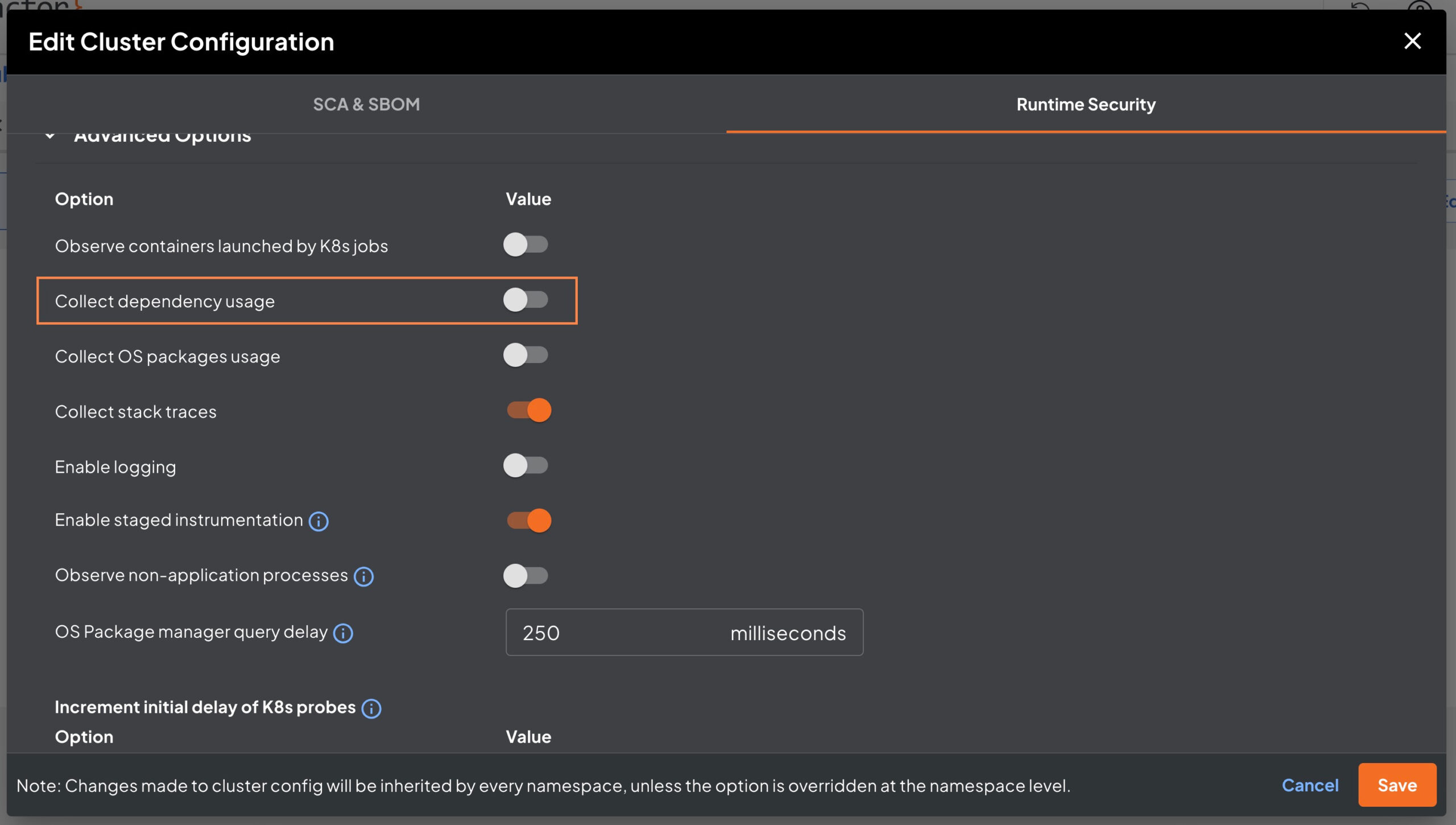
You can turn off this functionality by disabling Collect dependency usage option under Kubernetes Cluster -> Cluster config.
LSA Internals #
Deepfactor automatically detects the programming language per process and injects the appropriate language specific agent. As of today, Deepfactor provides LSA modules for applications written in either Java or Python.
Java Language Specific Agents
Deepfactor provides the following two java language specific agents
1. Java Virtual Machine Tools (JVM TI) Library: This is a lightweight JVM TI library that is used to collect java stack traces. This stack trace information is shown for the alerts raised by Deepfactor. Stack traces can be helpful for developers to pinpoint where the issue is within their code.
JVMTI agent is automatically injected by default since stack traces are enabled by default.
Ex.
dfctl run -a “my application” -c “my component” –version “111” -v –cmd /usr/bin/java -jar mycomponent.jar
2. Java Agent: This is a java agent which uses the Java Instrumentation API to gather runtime usage of dependencies. This information is shown under the usage section of the dependency. This information will help you understand the extent of usage of your dependencies and help you prioritize which vulnerable dependencies to update/replace.
At this time, the Deepfactor java-agent does not support a Java application that includes:
– non-JDK, or custom, ClassLoader(s) that do not use the default system ClassLoader ClassPool
– bytecode transformation/instrumentation
– operation with other java-agents
This agent is automatically injected when usage tracking is enabled.
Python Language Specific Agents #
Deepfactor provides a Python language specific agent that can be used to provide stack trace information for many alerts displayed in the Deepfactor management portal.
This agent is automatically injected when you enable stack traces.
Eg:
dfctl run -a “my application” -c “my component” –version “111” -v –cmd python3 myapp.py
The Python language specific agent works with Python versions 3.6 through 3.10, inclusive. It does not work with Python 2.x applications nor does it work with Python versions before 3.6. If stack traces are enabled for unsupported versions of Python, the language specific agent will not be loaded.
Note: The Python language specific agent generates stack traces for Deepfactor alerts by querying the Python interpreter to gather the trace. Depending on the Python modules installed and in use in the application at the time of the alert, you may or may not see Python stack traces for a given alert, for a given application. Further, Python will frequently report stack trace frames for internal modules that have been optimized out by the interpreter (these frames will typically be displayed as “bootstrap” frames in the Deepfactor portal). These limitations apply primarily to modules compiled from C code (CPython) or interpreter built-in code. Stack frames corresponding to user application files should be reported correctly in most cases.


