Deepfactor can scan your artifacts (source code or container images) and also observe running applications and generate alerts based on alert policies. Alert Policies are a list of configurable rules that you can use to tailor Deepfactor alerts according to your company’s or your application’s security policies. You can view/create alert policies by clicking on ‘Alert Policies’ in the left sidebar.
Alert policy categories #
Deepfactor provides different alert policies for static scans of your artifacts and runtime security of your running applications.
SCA & SBOM #
SCA and SBOM alert policies are comprised of a configurable set of rules that are evaluated against the results of the scans performed on your artifacts (source code or container images). A predefined uneditable policy “Built-in Policy- Standard” (default) is shipped along with the Deepfactor portal. It can be cloned to create custom policies. The policy is split into two categories:
- SCA: This category of rules are evaluated against the vulnerabilities associated with the resources present in your artifact.
- SBOM: This category of rules are evaluated against the metadata of the resources present in your artifact.
The following section describes how you can specify the policy while scanning your artifacts with Deepfactor
dfctl scan
Refer to dfctl scan usage to view how to pass the policy using the -p option.
Kubernetes/Webhook
You can specify the SCA & SBOM policy at cluster/namespace level from the webhook configuration UI under Kubernetes clusters.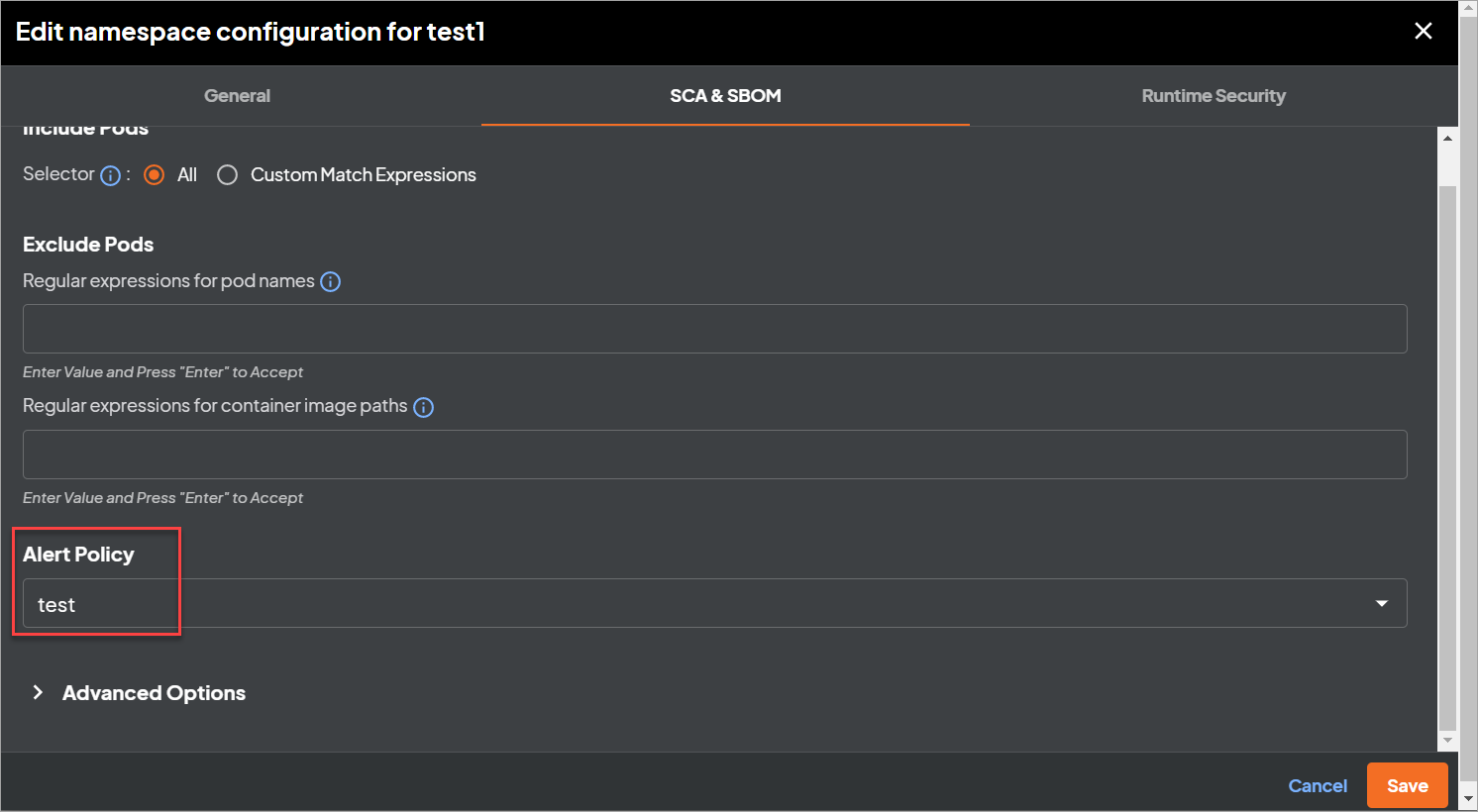
Runtime Security #
Runtime security alert policies are comprised of a configurable set of rules that are evaluated against the telemetry received from your running applications.. Two predefined uneditable policies “Built-in Policy- Standard” (Default) and “Built-in Policy- Max Alert” are shipped along with the Deepfactor portal. They can be cloned to create custom policies. The policy is split into multiple categories of rules based on the kind of vulnerability.
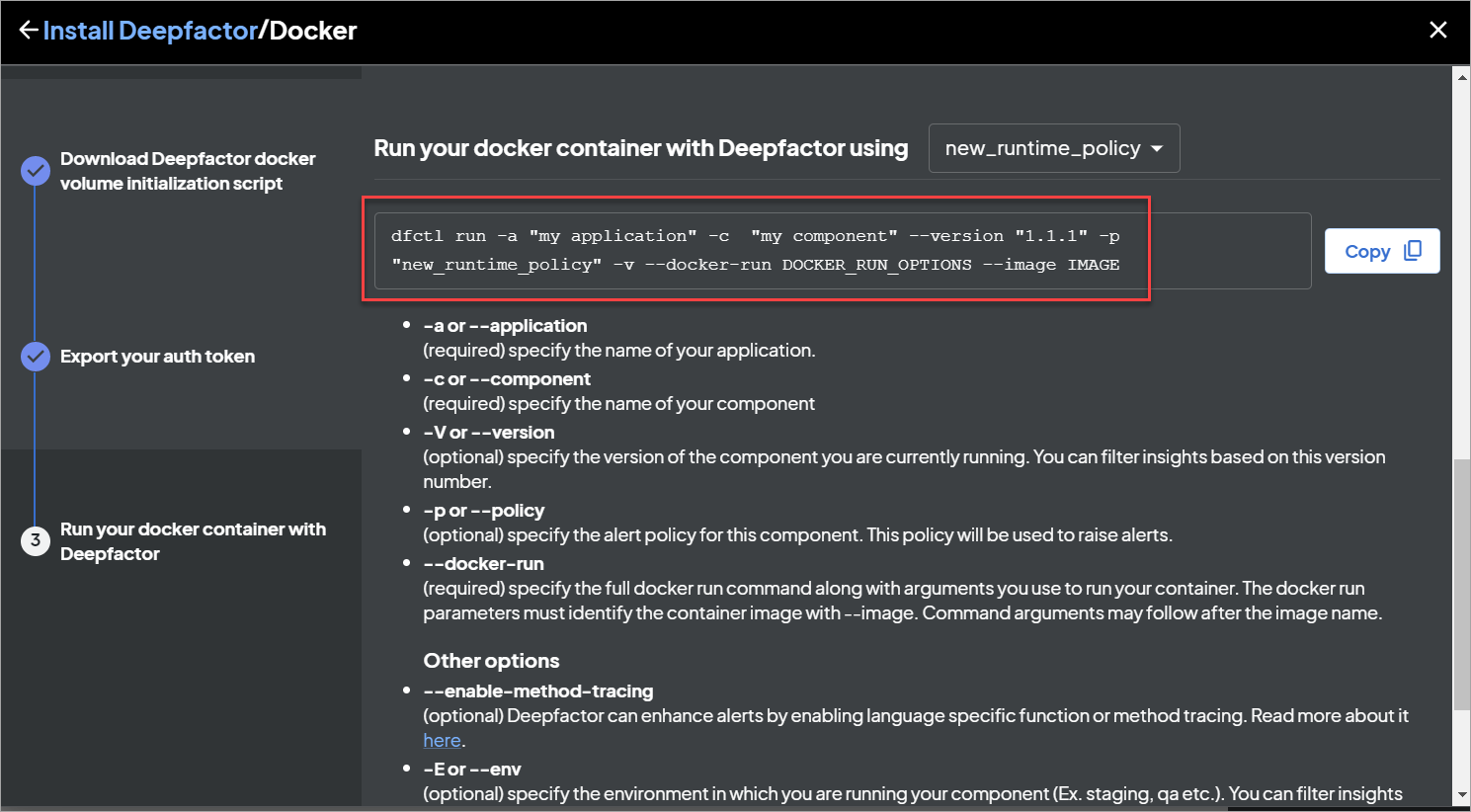
The following section describes how you can specify the policy while running your artifacts with Deepfactor
Kubernetes/Webhook
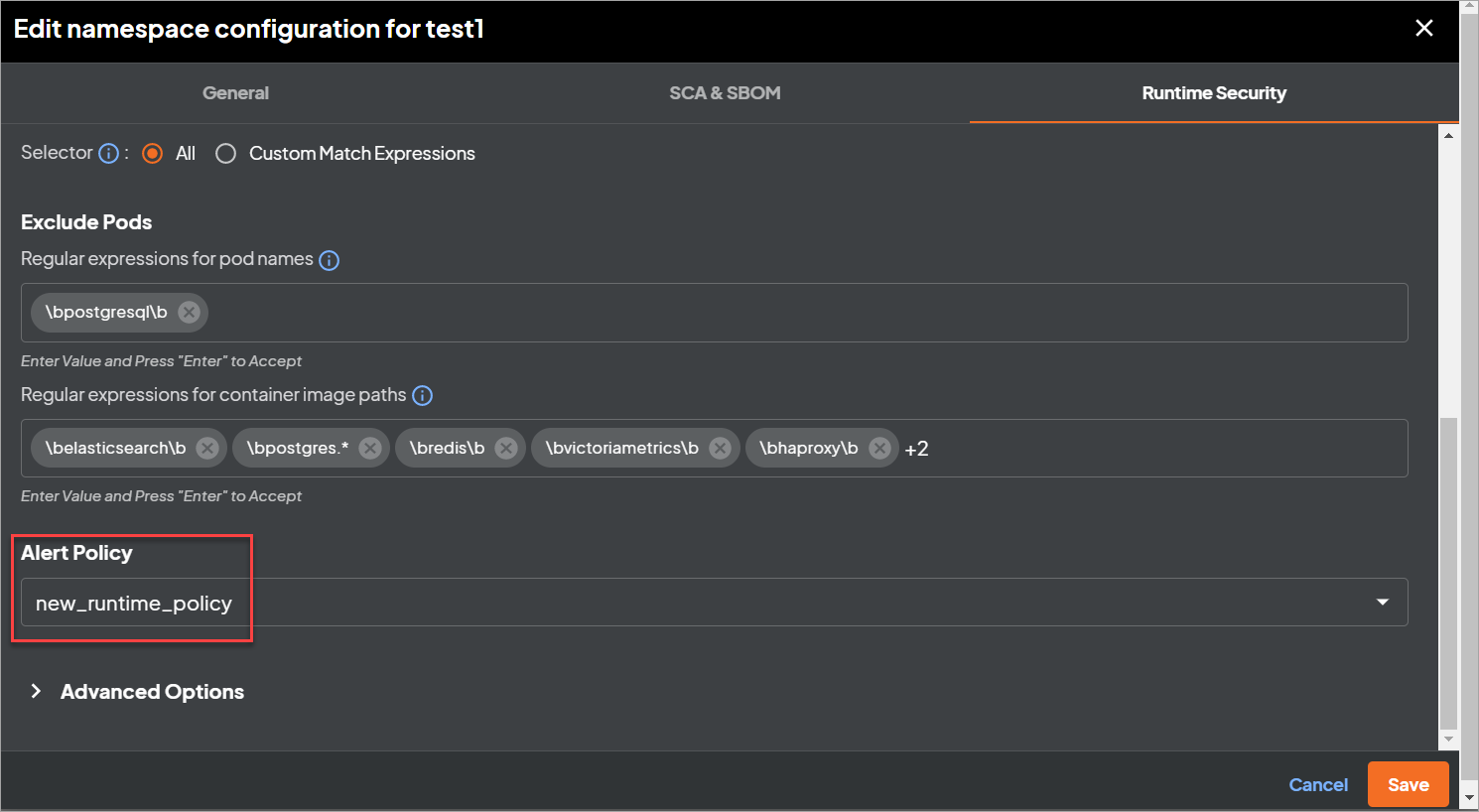
You can select the policy at cluster or namespace level from the webhook configuration UI under Kubernetes clusters
Containerized applications
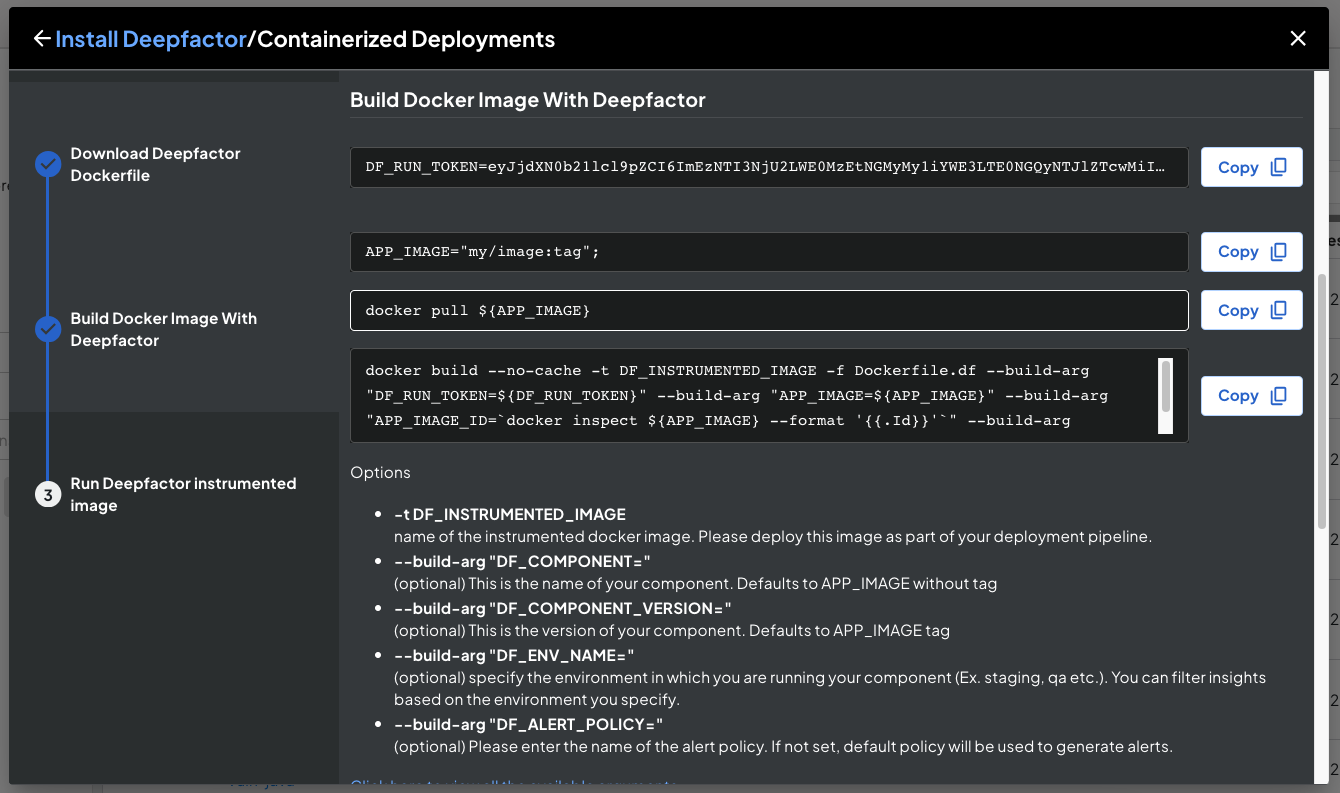
You can pass the name of the policy using the –build-arg “DF_ALERT_POLICY=name_of_the_policy” option when building a Deepfactor enabled container image.
Non Containerized
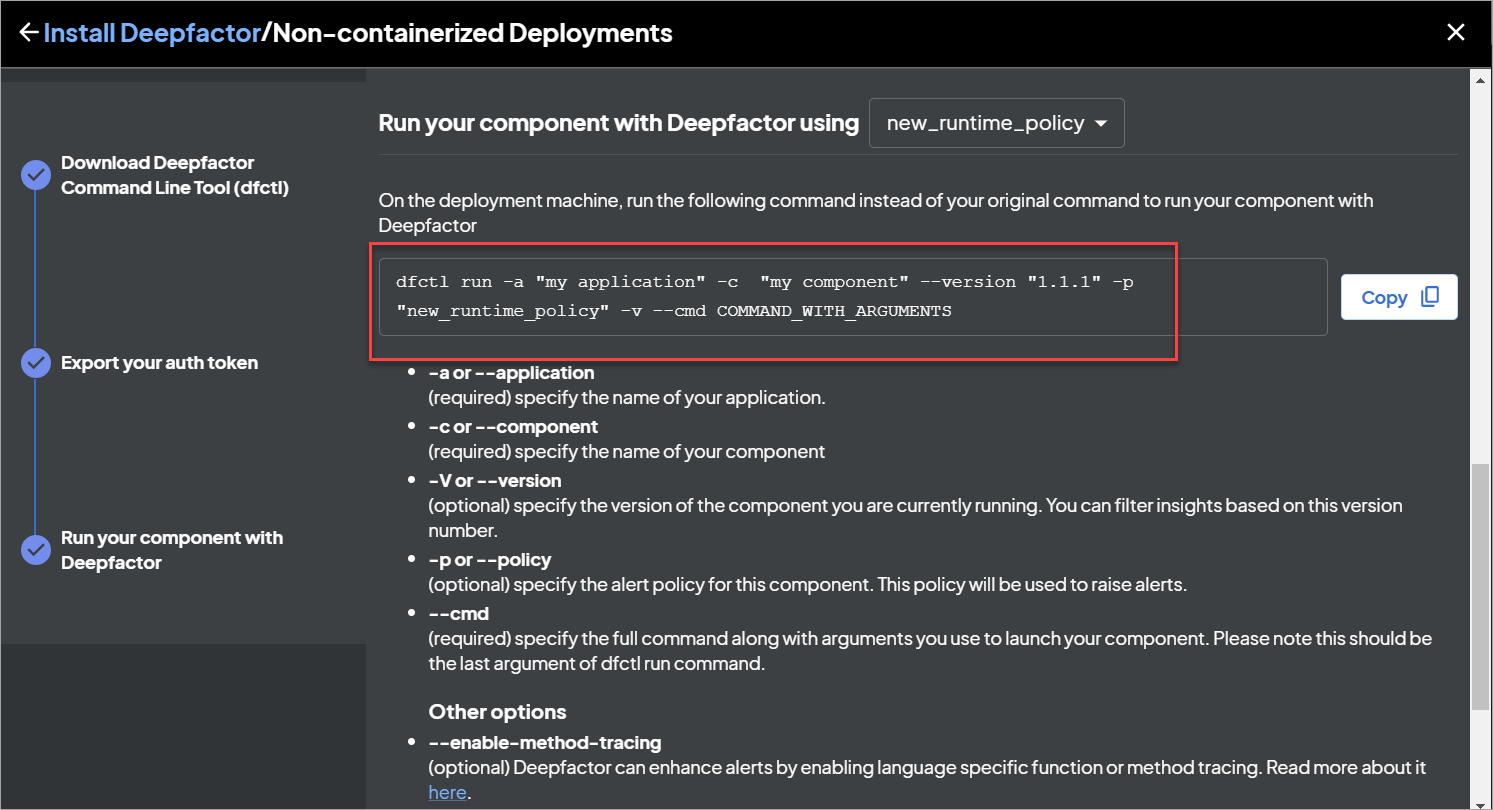
You can pass the name of the policy using the -p option when launching the non-containerized application using dfctl
Standalone Container image
You can pass the name of the policy using the -p option when launching the container using dfctl
Creating/editing custom alert policies #
You can click the “Clone” button to clone an existing policy. You can then edit this policy to turn on/off some rules or change the threshold/values of some rules. You can edit a custom alert policy (created by cloning) to enable/disable specific policies.
Note:
- While entering a list of values for a policy, you need to press the enter key after each value for it to be added to the list.
- Editing an alert policy will not affect existing alerts.


