Deepfactor can scan your artifacts (container images / file system directories) to generate SBOM and find SCA vulnerabilities. Deepfactor can also observe running containers / non-containerized applications to detect runtime risks. The unique capability Deepfactor provides is that it can correlate the results of the scan and runtime observation so you get
- An unified view of your application’s security posture
- Additional information so you can priortize which vulnerabilities to fix earlier than others.
Correlation Insights #
This section outlines some of the areas where Deepfactor correlates results from static scan and runtime observation.
In the application dashboard, you will be presented with the unified security posture of your application. Since Deepfactor also observes the running application, it can correlate usage information gathered at runtime with SCA information like vulnerabilities gathered during the static scan.
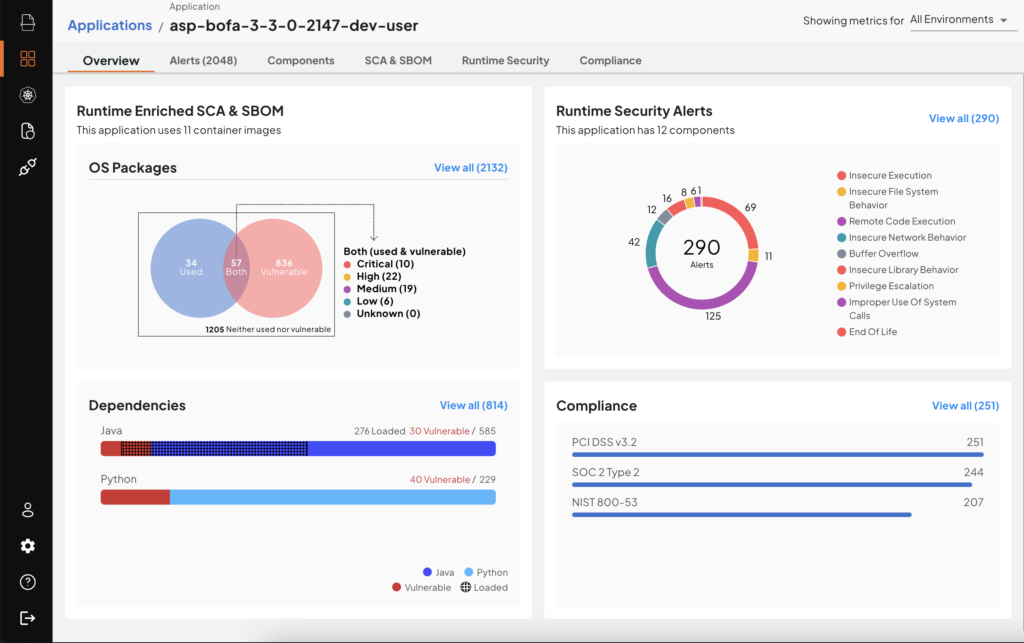
Application Dashboard with runtime enriched SCA & SBOM
OS Packages #
Deepfactor can intercept when a shared library is loaded by the application. Deepfactor then queries the package manager to find the OS package to which the shared library belongs. Deepfactor provides this usage information in multiple pages on the portal UI and also in API responses.
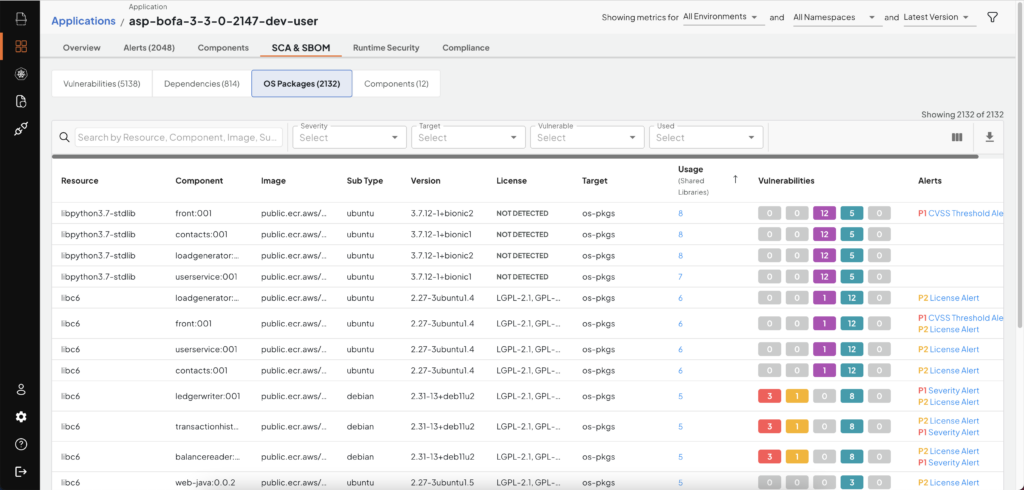
OS Packages with usage information
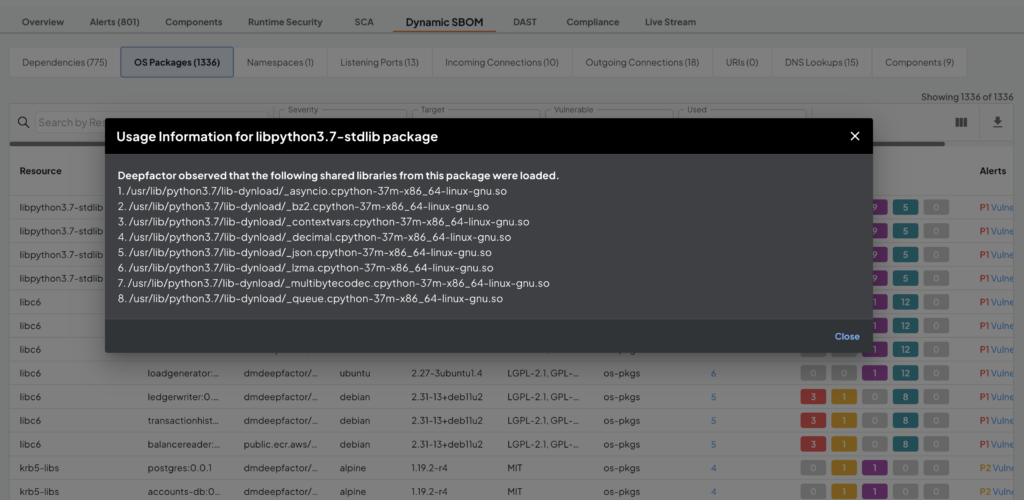
List of shared libraries opened
With Deepfactor, you will be able to get
- The full list of OS packages (SBOM) present in your application/container
- The list of vulnerable OS packages along with the vulnerability information
- The list of OS packages that are loaded by your application at runtime.
Actions you can take based on this information to improve your security posture are summarized in the table below.
| Vulnerable | Used | Recommendation | Notes |
| Yes | Yes | Update application code Upgrade OS package |
Since your application is using a vulnerable OS package, you will need to update your application code or software framework to ensure you use later versions of the OS package that has resolved the vulnerabilities. |
| Yes | No | Consider removing unused OS packages or finding an alternate base image. | Since your application is not using these OS packages, you can either remove them or find an alternate base image that does not have these OS packages. This will not only reduce the number of vulnerabilities in your container but also reduce the attack surface area. |
| No | Yes | No action needed | |
| No | No | Consider removing unused OS packages or finding an alternate base image. | Since your application is not using these OS packages, you can either remove them or find an alternate base image that does not have these OS packages. This will reduce the attack surface area. |
Application Dependencies #
Deepfactor also tracks the usage of application dependencies in the case of Java, Kotlin, Scala, Go, and interpreted language (python, Node.js, PHP, Ruby) dependencies. For java, Deepfactor injects a jvmti agent and intercepts class loaded event and then presents a list of all the classes that were loaded per java dependency. For interpreted language dependencies, Deepfactor shows the list of files loaded by the interpreter.
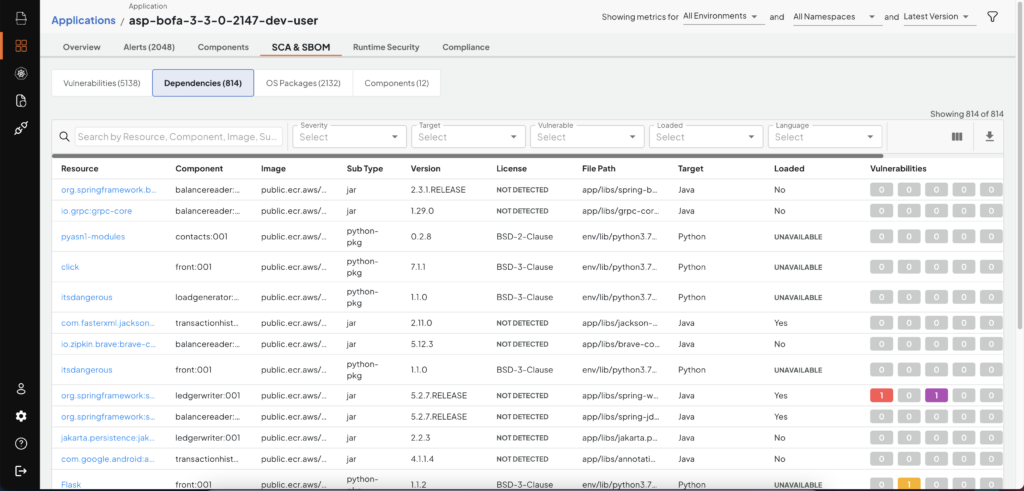
SBOM Dependencies with runtime usage
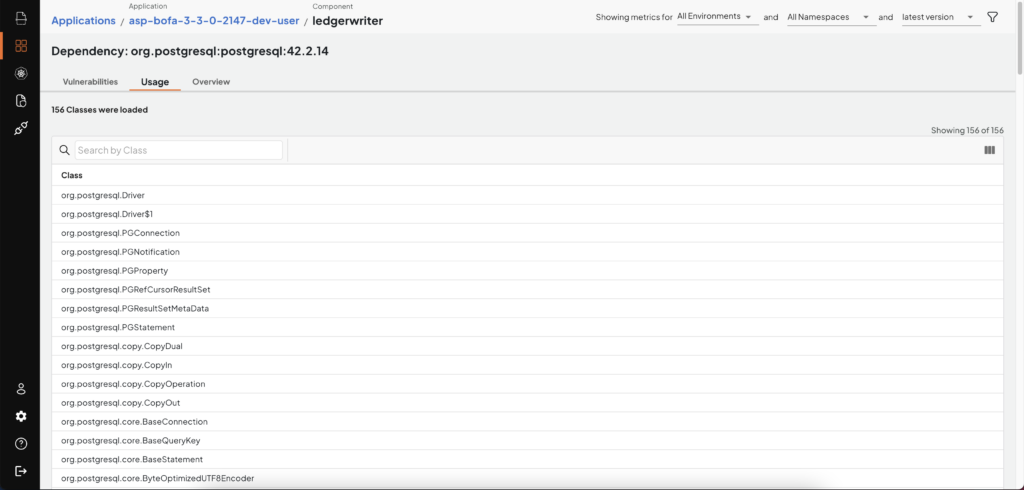
List of classes loaded per java dependency
Artifact Scan results #
On the artifact page, you will see the list of all the components that use the same artifact. This will help you understand where all this particular artifact is deployed.
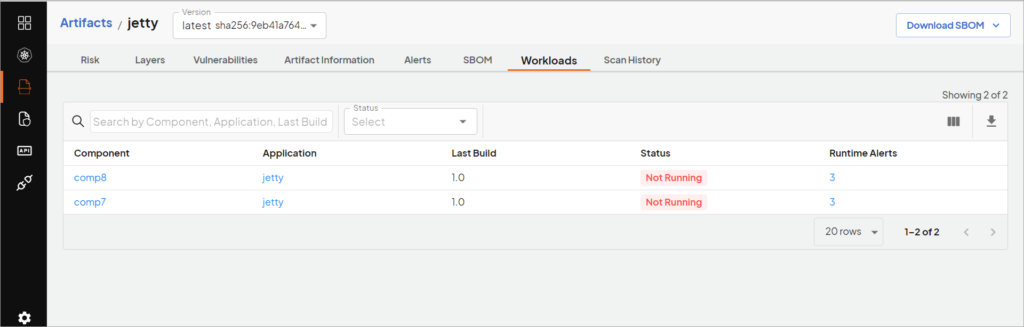
How does Deepfactor correlate artifacts with running applications/workloads? #
For container images, Deepfactor correlates based on the image ID. When a container is run using Deepfactor either using docker run or using K8s, Deepfactor attempts to get the image ID of the container that is being run. Deepfactor then shows the results of the scan performed on the image with the same image ID on the application and component dashboard. Hence it is important for Deepfactor to fetch the image ID of the running container to correlate results of the static scan. In K8s, Deepfactor deploys a scan pod which pulls the image’s manifest from the registry to get the image ID. If you are using private registries, you will need to provide the registry credentials as a K8s secret to enable the scan pod to pull the image manifest.
For file system scans, Deepfactor relies on the user to provide the same application name, component name and version for static scans and observing running applications. In other words, please pass the same application name, component name and component version to both dfctl scan and dfctl run commands so Deepfactor understands that the same artifact is being scanned and run and it can correlate results for you.
Example:
– Artifact: mydir/pythonapp (path to application code)
– Application: backend
– Component: pythonapp
– Version: 1.0
Static scan :
dfctl scan -s fs -a "backend" -c "pythonapp" -V "1.0" mydir/pythonapp
Runtime instrumentation:
dfctl run -a "backend" -c "pythonapp" -V "1.0" -v --cmd python run.py
Since the same application name, component name and version were passed to dfctl scan and dfctl run commands, Deepfactor can correlate results found in the two operations.

