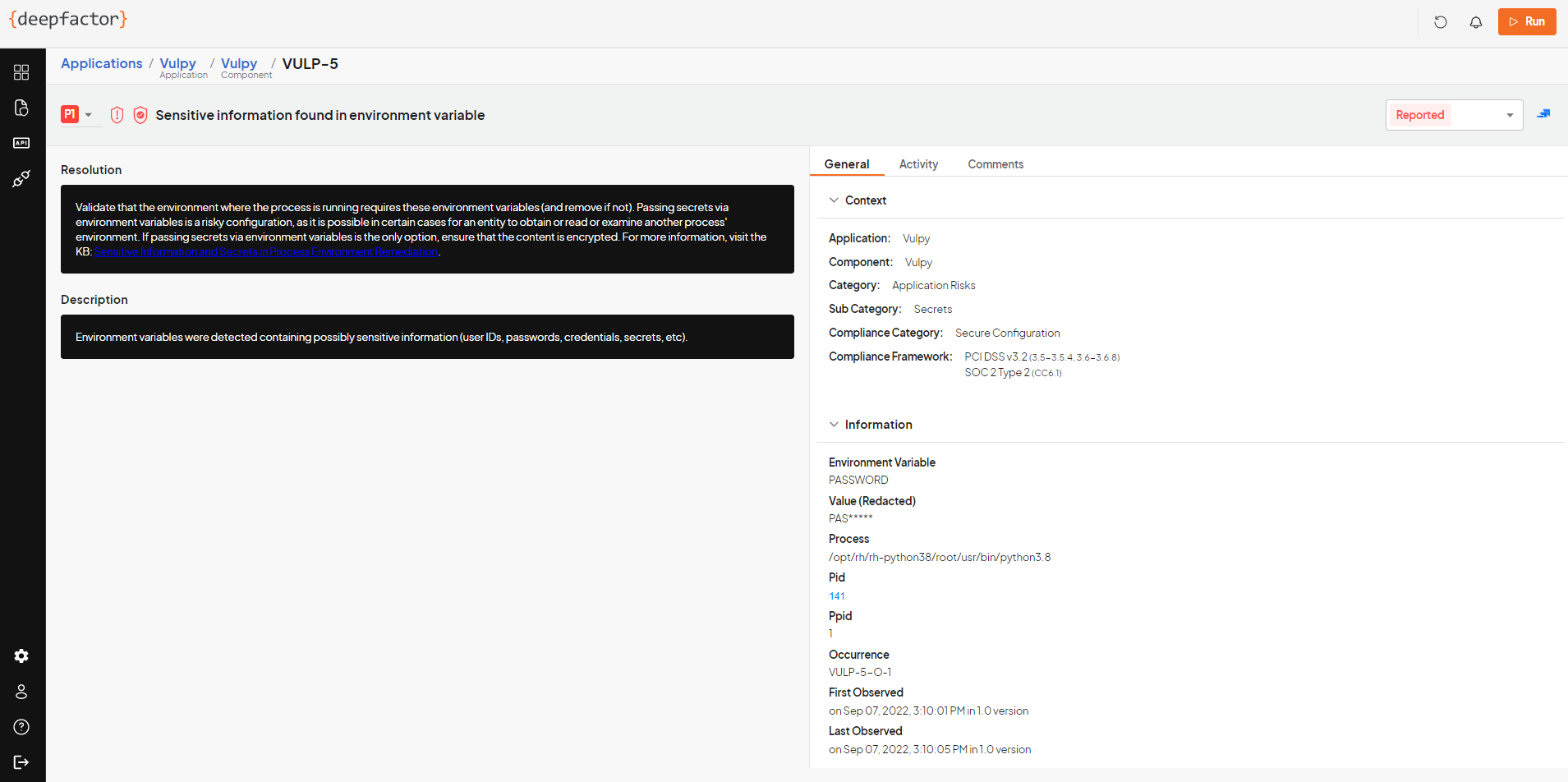
Passing secrets via environment variables may let an entity, in certain cases, obtain or examine another process’s environment. If passing secrets via environment variables, make sure that the content is encrypted and verify that the secret is needed by the process(es) within the environment.
Remediation Options
- Encrypt secrets passed via environment
- Store the secret in volume mount files or somewhere access is restricted/removed after the process has read it.
- Use a “Secrets as a service” solution.
- Rotate secrets/keys often.
Encrypt Secrets Passed via Environment
A decryption key will be required. A key or secret may be stored in a volume mount or temporary filesystem/keystore where access is restricted/removed after decryption key is read and used by the process that needs to decrypt the secret(s).
Restrict Access to Secret Material
Kubernetes: How to use secrets from volume mount files: Secrets: using-secrets-as-files-from-a-pod.
- Volume mounts can have restricted access and processes can drop privilege after access.
Added bonus: Secrets: mounted-secrets-are-updated-automatically
- Facilitates ease of key rotation.
Non-containerized VMs: remove access to secret key material after a secret is loaded/decrypted. e.g. leverage chroot, delete from temporary storage/memory.
Use a “Secrets as a service” Solution
From Best practices for managing & storing secrets like API keys and other credentials [2020]:
“Secrets management systems such as Hashicorp Vault or AWS Key Management Service are encrypted systems that can safely store your secrets and tightly control access.”


