What are Container Security Tools?
With the rise of cloud-native architectures and containerization technologies like Docker and Kubernetes, container security tools have become indispensable. These tools provide visibility and control over containerized workloads, operating across multiple layers of the container stack.
Container security tools are designed to monitor, analyze, and protect containerized environments from a range of security risks, including unauthorized access, data breaches, malware injections, and compliance violations. By examining activities within containers, these tools enable organizations to detect and mitigate insecure behaviors in file operations, network communications, process execution, and memory utilization.
The scope of container security tools extends throughout the entire lifecycle of cloud-native applications, from development and testing to production deployment. They play a pivotal role in ensuring the integrity, confidentiality, and availability of software workloads, fostering trust and resilience in modern application ecosystems. Container security tools are vital assets for security teams seeking to uphold regulatory compliance standards, mitigate emerging threats, and fortify the security posture of their containerized environments.
These tools essentially serve as the first line of defense against the evolving threat landscape faced by cloud-native applications, with capabilities that include real-time threat detection, vulnerability management, compliance enforcement, and incident response. As organizations continue to navigate the complexities of modern application architectures, the role of container security tools in safeguarding critical assets and mitigating security risks becomes increasingly important.
Key Features and Benefits
Container security tools offer several features and benefits essential for strengthening the security of cloud-native applications. These tools are equipped with a diverse set of capabilities designed to address the dynamic and evolving nature of security threats in containerized environments.
One of the primary features of container security tools is their real-time threat detection capability, which enables organizations to promptly identify and respond to malicious activities. By continuously monitoring container processes and analyzing runtime behaviors, these tools empower security teams to mitigate security incidents before they escalate, reducing the risk of data breaches and unauthorized access.
Additionally, container security tools facilitate vulnerability management functionalities, allowing organizations to proactively identify and remediate security flaws across their containerized workloads. Through continuous monitoring and analysis of container activities, these tools assist in identifying vulnerabilities in both application code and third-party dependencies, thereby reducing the attack surface and minimizing risk.
Regulatory Compliance
Container security tools play a crucial role in helping organizations meet regulatory compliance requirements. By enforcing necessary controls, monitoring mechanisms, and audit capabilities, these tools enable organizations to adhere to industry-specific standards such as SOC 2, PCI-DSS, NIST, and ISO. This ensures that applications deployed in containerized environments maintain compliance with regulatory mandates and industry best practices.
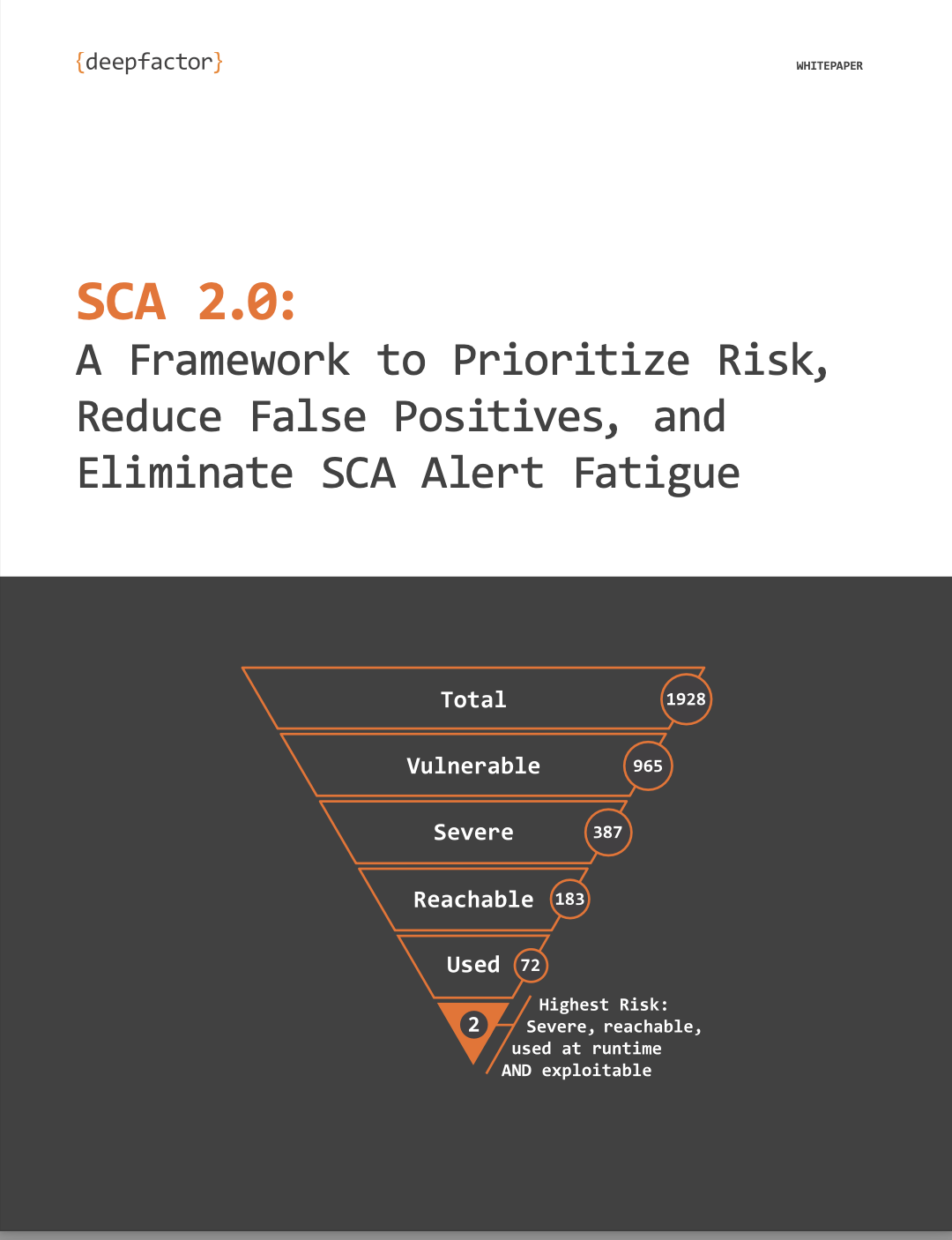
Furthermore, container security tools contribute to the adoption of a defense-in-depth approach to application security. By integrating seamlessly with existing security controls such as secure coding practices, network security, and access controls, these tools provide an additional layer of protection against cyber threats. This multi-layered security strategy enhances the overall resilience of cloud-native applications and reduces the likelihood of successful attacks. Container security tools help alleviate alert fatigue and improve operational efficiency by leveraging runtime correlation and behavioral analysis. By prioritizing security alerts and minimizing false positives, these tools streamline the remediation process and optimize resource allocation. This enables security teams to focus their efforts on addressing critical vulnerabilities and strengthening the security posture of containerized environments.
The key features and benefits offered by container security tools are essential for organizations seeking to safeguard their cloud-native applications against emerging security threats. From real-time threat detection to compliance enforcement and operational efficiency, these tools play a pivotal role in mitigating security risks and ensuring the resilience of containerized workloads.
Challenges and Considerations
Implementing container security tools can pose several challenges and considerations for organizations seeking to fortify their cloud-native environments. These challenges stem from the evolving threat landscape faced by modern applications.
One of the primary challenges organizations encounter is the complexity associated with deploying container security tools; traditional runtime security tools may struggle to adapt to the short-lasting nature of containerized workloads. Integrating container security tools with existing toolchains can present integration challenges, limiting effectiveness.
Maintaining agility and application delivery speed while implementing container security measures can be a significant consideration for organizations. Traditionally, security has been perceived as a bottleneck in the software development lifecycle (SDLC), with security controls often slowing down development processes. Balancing the need for security with the imperative for rapid innovation requires organizations to adopt DevSecOps principles and integrate security seamlessly into the development pipeline.
Compatibility Issues
Ensuring compatibility with Kubernetes platforms and other container orchestration tools poses a challenge for organizations deploying container security tools. Some runtime security solutions may not be compatible with Kubernetes platforms or environments without access to underlying host infrastructure, limiting their effectiveness and usability in certain deployment scenarios.
Bridging Cultural Gaps
Addressing the relationship between developers and security teams is a critical consideration for organizations embracing DevSecOps principles. Security controls must be designed to align with the speed and scale of cloud-native applications, empowering developers to prioritize security without impeding development velocity. Bridging this gap requires collaboration between development, operations, and security teams and providing developers with the tools and resources they need to integrate security into their workflows.
Conclusion
Container security tools play a pivotal role in safeguarding the integrity, confidentiality, and availability of cloud-native applications in dynamic and ever-evolving environments. These tools, encompassing a broad range of solutions designed to monitor, analyze, and protect containerized environments, offer a comprehensive approach to addressing security challenges throughout the application lifecycle.
There are many benefits to container security tools; they enable real-time threat detection, empowering organizations to promptly identify and respond to malicious activities. Additionally, these tools facilitate vulnerability management, assisting in the identification and remediation of security flaws across containerized workloads. Moreover, container security tools contribute to regulatory compliance efforts, ensuring that applications adhere to industry-specific standards and best practices. By integrating with existing security controls, these tools enhance the overall resilience of cloud-native applications, reducing the likelihood of successful cyber attacks.
However, the implementation of container security tools is not without challenges. Deploying these tools in dynamic environments can be complex, especially when traditional security solutions struggle to adapt to the ephemeral nature of containers. In navigating these challenges, organizations must adopt a holistic approach to container security, balancing security requirements with rapid innovation and development velocity. By addressing deployment complexities, integration challenges, and cultural barriers proactively, organizations can effectively mitigate security risks and ensure the resilience of their containerized environments. Container security tools, with their diverse set of capabilities and benefits, are crucial assets in the quest to secure cloud-native applications against emerging threats in today’s dynamic digital landscape.
FAQs
What are container security tools and why are they important?
Container security tools are specialized software designed to monitor, analyze, and protect containerized environments from various security threats such as unauthorized access, data breaches, malware injections, and compliance violations. They operate across multiple layers of the container stack, providing visibility and control over containerized workloads. These tools are important because they help ensure the integrity, confidentiality, and availability of cloud-native applications, which are essential for maintaining trust and resilience in modern application ecosystems.
How do container security tools help with regulatory compliance?
Container security tools assist organizations in meeting regulatory compliance requirements by enforcing necessary controls, monitoring mechanisms, and audit capabilities. They help ensure that applications deployed in containerized environments adhere to industry-specific standards such as SOC 2, PCI-DSS, NIST, and ISO. By doing so, these tools ensure that organizations maintain compliance with regulatory mandates and industry best practices, reducing the risk of penalties and enhancing overall security posture.
What challenges might organizations face when implementing container security tools, and how can they address them?
Organizations may face several challenges when implementing container security tools, including the complexity of deployment, integration with existing toolchains, maintaining agility and application delivery speed, and ensuring compatibility with Kubernetes platforms and other container orchestration tools. To address these challenges, organizations should adopt DevSecOps principles, which integrate security seamlessly into the development pipeline, and foster collaboration between development, operations, and security teams. Additionally, choosing container security tools that are specifically designed for cloud-native environments and offer compatibility with common orchestration tools can help mitigate these issues.
Free Live demo
Experience the power and efficiency of the Deepfactor Application Security Platform through a live, interactive demo.
SIGN UP TODAY! >