What is Software Composition Analysis (SCA)?
Software Composition Analysis (SCA) tools are essential for identifying and managing vulnerabilities in open-source components and third-party libraries within software applications. These tools scan codebases and container images, analyze code dependencies, and flag potential security vulnerabilities and licensing issues. Despite their importance, these tools can sometimes overwhelm engineering and application security teams with excessive false positives, leading to alert fatigue.
Key Features and Benefits of Software Composition Analysis
SCA tools offer a range of features and benefits essential for identifying and managing vulnerabilities in open-source components and third-party libraries within software applications:
Real-time Vulnerability Detection: SCA tools enable real-time identification of vulnerabilities by scanning codebases and container images for known security issues. This proactive approach helps organizations quickly address vulnerabilities, reducing the risk of exploitation.
Comprehensive Dependency Analysis: SCA tools conduct thorough dependency analysis to identify all components and libraries used within an application. This comprehensive view enables organizations to accurately assess their software security posture and identify potential risks associated with each dependency.
Licensing Compliance Management: In addition to identifying security vulnerabilities, SCA tools help organizations manage licensing compliance by detecting and flagging license conflicts or violations within software components.
Automated Risk Prioritization: SCA tools automate the prioritization of security risks, typically using CVSS severity and EPSS exploitability scores. By categorizing vulnerabilities according to their potential impact and likelihood of exploitation, organizations can focus their remediation efforts on addressing the most critical issues first.
Integration with DevSecOps Pipelines: SCA tools seamlessly integrate into DevSecOps pipelines, allowing organizations to incorporate security checks into the software development lifecycle. By automating security scans and vulnerability assessments at various stages of development, organizations can identify and remediate issues early, reducing the risk of security breaches in production.
Reduced Alert Fatigue: By accurately prioritizing security alerts and minimizing false positives, certain SCA tools can help alleviate alert fatigue among engineering and application security teams. This ensures that developers can focus their efforts on addressing genuine security issues without being overwhelmed by excessive notifications.
Enhanced Compliance and Governance: SCA tools support compliance efforts by providing visibility into the use of open-source components and ensuring adherence to licensing requirements and industry regulations. This enables organizations to maintain regulatory compliance and mitigate legal risks associated with non-compliant software.
Continuous Monitoring and Reporting: SCA tools offer continuous monitoring capabilities, allowing organizations to track changes in software dependencies and detect new vulnerabilities as they emerge. Additionally, these tools generate comprehensive reports that provide insights into the application security posture, facilitating informed decision-making and risk management.
Improved Software Security and Resilience: Overall, SCA tools contribute to improved software security and resilience by helping organizations identify, prioritize, and remediate security vulnerabilities effectively. By proactively managing software composition risks, organizations can strengthen their defense against cyber threats and safeguard sensitive data and assets.
Challenges with Legacy SCA Tools
While Software Composition Analysis tools offer significant benefits for identifying and managing vulnerabilities in software applications, they also present challenges and considerations that organizations need to address:
Alert Fatigue: Alert fatigue is one of the primary challenges associated with SCA tools. Developers and security teams often become overwhelmed by the high volume of alerts these tools generate, leading to critical issues being overlooked or incorrectly prioritized due to the sheer volume of notifications.
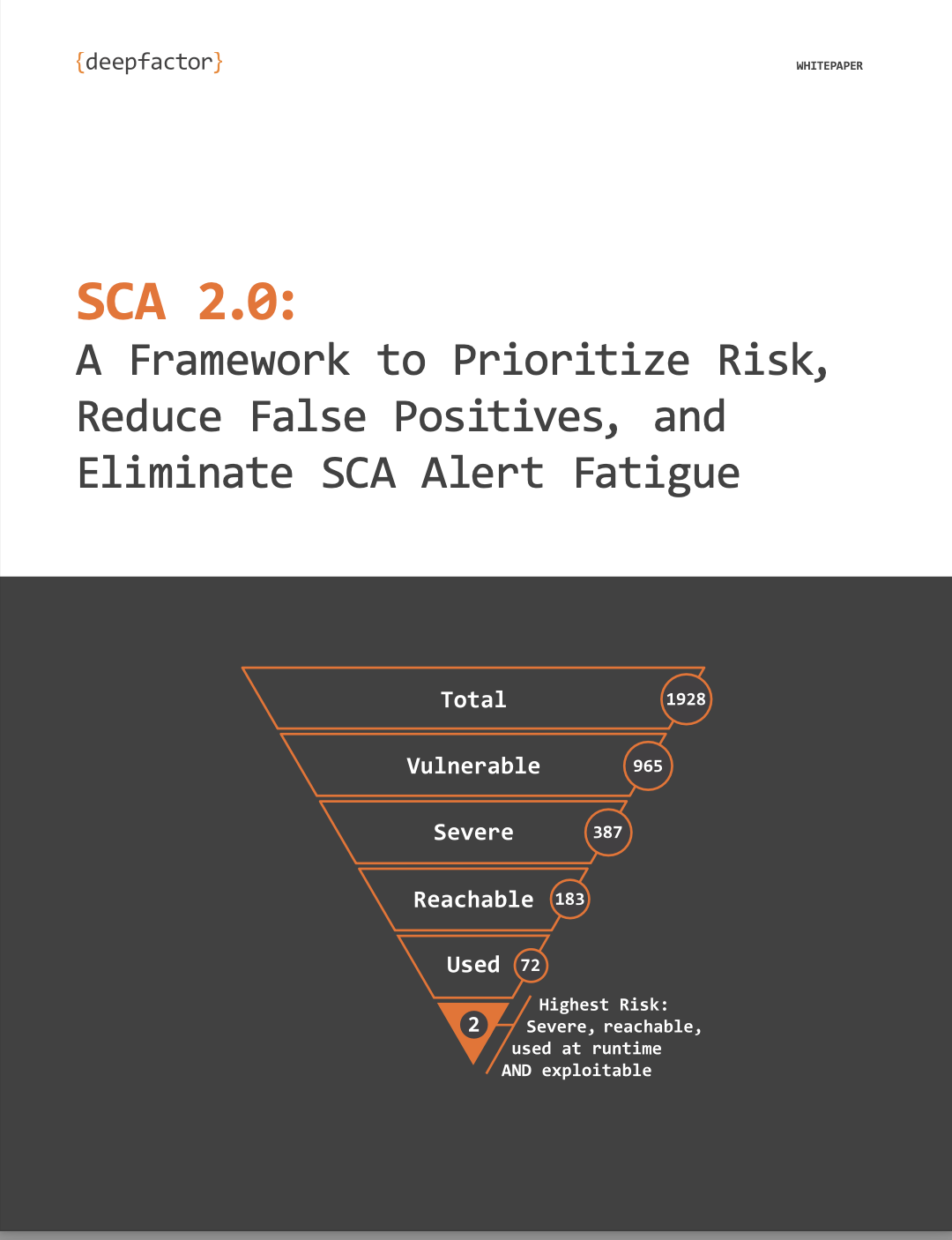
Lack of Context: Another significant challenge is the lack of contextual information provided by SCA tools. Most SCA tools prioritize based on severity and exploitability (CVSS and EPSS scores), which can result in numerous alerts with the same level of urgency. Developers struggle to identify which vulnerabilities pose the highest risk and need to be addressed first, as they lack additional details and context about which vulnerabilities are not only severe and exploitable but also reachable and used at runtime. This inefficiency prolongs the process of remediating the highest-risk vulnerabilities first.
Complex Dependency Analysis: Modern applications’ reliance on numerous dependencies and third-party libraries complicates the accurate assessment of the entire software stack’s security posture. The complexity of dependency analysis can lead to incomplete or inaccurate vulnerability assessments, leaving organizations vulnerable to undiscovered risks.
Integration Limitations: Integrating SCA tools into existing development workflows presents another challenge, particularly in agile or DevOps environments where speed and efficiency are paramount. Ensuring seamless integration with CI/CD pipelines and development tools requires careful planning and coordination to minimize disruption to the software development lifecycle. Traditional SCA tools focus primarily on static analysis of codebases and container images, providing limited visibility into runtime behavior. This limitation means that dynamic security risks, which only manifest during application execution, such as runtime dependencies or configuration vulnerabilities, may be overlooked.
Addressing these challenges and considerations requires a holistic approach to software composition analysis, encompassing technical solutions, process improvements, and organizational initiatives to enhance the effectiveness and efficiency of SCA practices. By proactively addressing these challenges, organizations can maximize the benefits of SCA tools while mitigating potential risks.
Mitigating Alert Fatigue with SCA 2.0
To address alert fatigue, application security teams must enhance the accuracy of vulnerability detection, reduce false positives, prioritize alerts across multiple variables, and provide more contextual information with each alert. Customizable alert thresholds and prioritization mechanisms enable developers to filter and focus on critical alerts, optimizing resource allocation. Integrating the newest and next-generation SCA tools into software development workflows and correlating findings with runtime behavior offers actionable guidance for vulnerability remediation, enhancing efficiency without overwhelming developers.
SCA 2.0 Framework for Prioritizing Alerts
An effective way to improve the rate at which engineering teams fix critical security vulnerabilities and eliminate alert fatigue is to continuously and automatically filter and prioritize security alerts. The SCA 2.0 framework proposes six strategies for prioritizing SCA alerts to reduce alert fatigue and enhance remediation efforts:
- Severity: Assessing the potential impact and consequences of vulnerabilities to prioritize patching and resource allocation.
- Usage: Determining whether vulnerable components are actively used to reduce false positives and focus on high-risk issues.
- Reachability: Analyzing how vulnerabilities can be exploited via different code paths to guide remediation efforts effectively.
- Exploitability: Evaluating the ease of exploiting vulnerabilities to allocate resources for security measures appropriately.
- Applicability: Assessing the relevance of vulnerabilities to specific application components and configurations for prioritization.
- Topology: Understanding deployment architecture to prioritize remediation based on the likelihood of exploitation.
Implementing these strategies empowers organizations to streamline vulnerability management, reduce alert fatigue, and fortify their software against emerging threats.
Conclusion
Software Composition Analysis tools play a vital role in modern application security by identifying and managing vulnerabilities in open-source components and third-party libraries. However, the adoption of SCA tools presents both opportunities and challenges for organizations striving to enhance their software security posture.
The benefits of SCA tools, including improved vulnerability management, enhanced compliance, and reduced security risks, are undeniable. By leveraging SCA tools, organizations can gain valuable insights into their software supply chain, identify potential security threats, and mitigate risks associated with third-party dependencies. Moreover, SCA tools enable organizations to comply with regulatory requirements and protect intellectual property rights, fostering trust and confidence among stakeholders.
Despite these benefits, organizations must navigate various challenges and considerations when implementing SCA practices. Alert fatigue, false positives, and the complexity of dependency analysis can hinder the effectiveness of SCA tools and overwhelm development teams. Integration with development workflows, scalability, and legal compliance are additional factors that organizations must address to maximize the value of SCA tools while minimizing associated risks.
To overcome these challenges and optimize SCA practices, organizations should consider tools and frameworks that enable them to focus on improving accuracy, reducing false positives, and prioritizing vulnerabilities based not only on severity and exploitability but also on reachability and usage at runtime, for true prioritization of highest-risk vulnerabilities. Seamless integration with development pipelines, continuous monitoring, and proactive risk management are essential for ensuring the effectiveness and sustainability of SCA initiatives.
FAQs
Free Demo Signup
Experience the power and efficiency of the Deepfactor Application Security Platform through a live, interactive demo.
SIGN UP TODAY! >