Though many organizations successfully (more or less) navigated the transition to DevOps, addressing security challenges in cloud native applications remains a major challenge. In order to address these challenges, over 60% of organizations have started to incorporate security throughout the software development lifecycle (SDLC). The drivers behind “shifting left” are obvious—engineering teams are responsible for driving the business; therefore information security must adapt to development processes and tools, not the other way around.
However, given the unique characteristics of cloud native applications, combined with increased release velocity, the adoption of security and compliance by development teams remains … well, undeveloped. In fact, according to the Secure DevOps and Misconfigurations 2021 Report by the Cloud Security Alliance, only 30% of security professionals admit to “fully implementing DevSecOps,” meaning most organizations are struggling to escape the “ideation and planning” stage. And though 42% of respondents hope to address these shortcomings in 2022, the further adoption and maturity of DevSecOps will continue to have immense opportunity for growth.
These plans notwithstanding, many companies continue to struggle with assessing progress and identifying the necessary steps and programs to evolve. In order to address these challenges, as reported by Gartner in the Innovation Insight for Cloud-Native Application Protection Platforms (for which Deepfactor CMO, Seth Knox, wrote an excellent blog post, What is a CNAPP?), some organizations have decided to “manually [stitch] together 10 or more disparate security tools—some old and some new—each with siloed responsibility and view of application risk.” This creates a tedious, disjointed security pipeline for engineering teams to manage, often providing results in the later stages of the SDLC.
In reality, “true” DevSecOps requires so much more than shifting traditional, heavyweight application security tools and processes onto developers … especially 10 of them! Rather, realizing the full advantages of securing applications in development requires purposeful planning for evolving beyond the current, time-consuming checkpoints offered with legacy platforms. This starts with an honest assessment of your organization’s existing toolchain and culture:
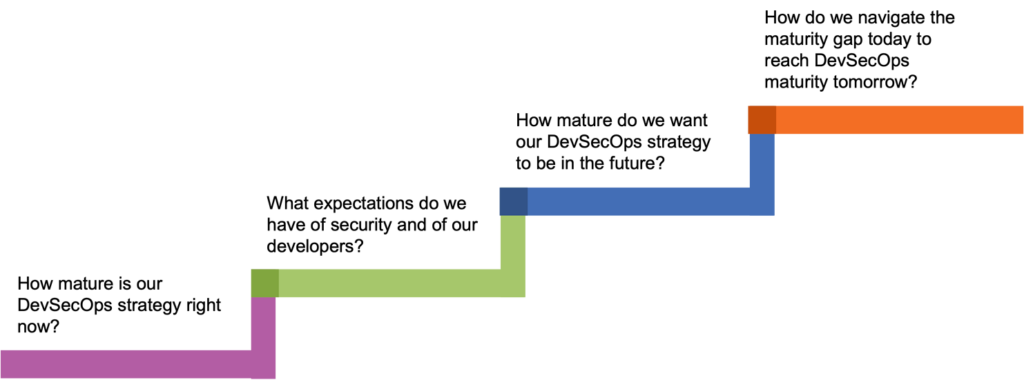
For better or worse, answering these questions often uncovers … “uncomfortable truths” about your enterprise’s strategy or framework for DevSecOps. From outdated technology with incomplete-to-nonexistent automation; dysfunctional processes for prioritization and remediation; and strained communication between development and security, there exists substantial challenges for organizations to navigate. Managing the balance between security and the agility and flexibility of modern development practices has never been more important.
Fortunately, immature organizations struggling to implement a developer-friendly security pipeline have several avenues to consider as they aim to improve their DevSecOps strategy:
- Culture & Education—By removing the friction between development, operations, and security, organizations can ensure security considerations are not overlooked—vulnerabilities are removed/upgraded, insecure code is identified early, and developers are well-trained (by security champions) in the development of secure and compliant applications.
- Cloud Native Risks & Tools—Engineering teams tasked with ensuring application and data security should be open to using next-generation tools (e.g. CNAPP), to integrate security and compliance testing seamlessly into the DevSecOps toolchain, ensuring the discovery, prioritization, and remediation of security insights during development and test.
- Integration & Automation—By ensuring security tools are fully-integrated into the CI/CD pipeline, developers and security teams can automate testing, creating a process with repeatability, consistency, and auditability. This allows developers to focus on delivering value rather than repeating manual efforts, potentially leading to vulnerabilities and insecure code shipping into production.
Many organizations initially focus on the mechanism through which application code and infrastructure is scanned and analyzed for security insights. However, given the challenges outlined in the opening paragraphs, the result is often a complex set of overlapping and loosely-integrated tools spanning development and production. It’s for this reason many engineering teams have started to evaluate application security platforms purpose-built to address the requirements of cloud native applications and developers.
These challenges and considerations are the driving force behind developer security platforms such as Deepfactor. Instead of creating a complex set of overlapping and loosely-integrated tools spanning development and production, organizations should be evaluating tools that 1) integrate security and compliance testing seamlessly into DevSecOps, 2) educate developers with contextual and actionable security insights, and 3) help create a security culture within the engineering organization. In terms of maturation, developer security opts to replace “shift left” with “start left,” minimizing friction for developers and identifying critical data early in development when the stakes are highest.

Join us Thursday, May 5th from 2:00-2:45 ET / 11:00-11:45 PT as we continue this conversation! You can register here to join us.
The objective of this webinar is to expand on the challenges described above, and to offer engineering leaders the guidance necessary to reach DevSecOps Maturity:
- Identifying the various markers to determine DevSecOps maturity
- Why relying on static scanning tools to detect vulnerabilities isn’t enough
- Understanding the value of automating security controls in you CI/CD pipeline
- The importance of including culture and education in your “shift left” strategy
- What do Cloud Native Application Protection Platforms (CNAPP) mean for the future of application security and the adoption of DevSecOps?





